
Keep your web applications continuously secure
Discover problems like SQL injections, XSS, outdated libraries, and weak authentication before attackers do. Catcher24 continuously scans your apps and translates the findings into clear recommendations in your dashboard.
Trusted by companies and organizations from various sectors: Catcher24 offers practical insights that are directly applicable.

What is web application scanning?
Modern web applications are complex, dynamic, and often the main entry point to your business. They are used extensively by customers, employees, and partners, making them a popular target for attackers.
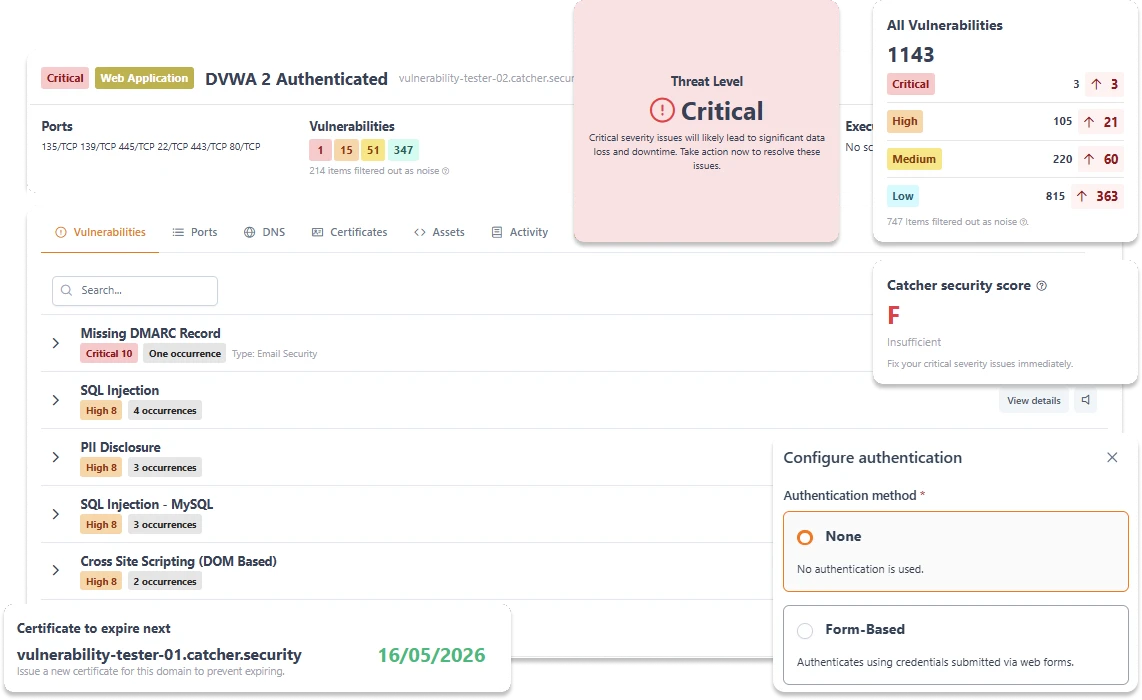
Catcher24 continuously tests your applications for critical security flaws such as SQL injections, XSS, outdated libraries, and weak login processes. These comprehensive pentests are fully automated, so you don't have to manually analyze code.
You get insight into the most important risks, a clear overview in your dashboard, and concrete advice on how to fix them. This way, you can keep rolling out releases while Catcher24 monitors security.
What is included in our web application scanner?
Web apps are constantly changing. New features, integrations, and frameworks, or a missed update of your organization's web applications, bring new risks. Catcher24 scans them automatically, so you always know if your apps are still secure.
SQL Injection
Protection of your data
An SQL injection can give attackers direct access to your database. Catcher24 automatically detects these vulnerabilities and helps you prevent sensitive customer and company data from being stolen.

Cross-Site Scripting (XSS)
Secure user experience
XSS attacks use malicious scripts to hijack user sessions or steal data. Catcher24 identifies these flaws and provides advice, so your users remain protected and your reputation is not at stake.

Authentication
Reliable authentication
Weaknesses in login processes can lead to account takeovers. Catcher24 checks if your authentication is set up correctly, detects session hijacking or weak passwords, and helps you ensure that only the right people get access.

Outdated libraries
Stay up-to-date and secure
Many web apps run on open-source libraries. If they are outdated, they are an easy entry point for attackers. Catcher24 detects which versions you are using and warns you about known vulnerabilities, so you can patch in time.


How our web application scanner works
Catcher24's web application scanner performs a very extensive pentest, works fully automatically, and seamlessly integrates with the development process and secure management of your important applications. From setup to scan reporting, it's simple, clear, and always up-to-date.


Supports authenticated scans.

Works with single-page applications and APIs.

Scans your JavaScript frameworks and other libraries.

The importance of scanning web applications
Web applications are often the first targets of hackers. They are visible, used intensively, change quickly, and often contain personal data. You want to minimize the risk of data loss or misuse of your organization's or customers' data. Therefore, security should never be an afterthought.

Web apps are the main entry point for attackers.

External libraries carry risks.

Security without slowing down your development team.

Customer success stories
While Catcher’s self-service tool offers powerful vulnerability scanning, our advanced integrations are only available with our managed service through trusted partners.

Our intergrations
Available with managed services via Catcher24 certified partners.

Partner integration
Phishing simulations
Integrate phishing campaigns and security awareness training with Phished.

Partner integration
Endpoint protection
Expand your security with endpoint protection via ESET.
Frequently asked questions
"Pentest" is short for "penetration testing." Our automatic web application scanner uses the same methods as cybercriminals to look for weak spots in a website, application, or IT infrastructure. The scan finds and reports vulnerabilities so you can fix them before malicious actors can exploit them.
We recommend scheduling scans regularly, at least once a month, with real-time notifications for any new vulnerabilities that arise.
Infrastructure scan: checks servers, networks, and cloud settings for OS and service vulnerabilities.
Web application scan: tests websites and APIs for application-specific flaws such as SQL injection and XSS.
Consult our help article for a further explanation of the different types of scans.
Yes. The scanner also works with SPAs and APIs, and can scan JavaScript frameworks and other external libraries.
Authenticated scans are scans in which the scanner gains access to parts of the application that require a login or certain permissions. This allows the scanner to also look for vulnerabilities that are behind an authentication layer, for example, in dashboard functions.
Yes, if they are publicly accessible. It is even recommended to use your development/staging as production environments. The scan also tries to perform database injections and can thus damage your database.


Improve your cybersecurity today
Start your free trial now and discover what Catcher 24 can do for your company. No credit card required, no installation. Just real insight into your real risks.











